Overview:

Azure Application proxy provides single sign-on (SSO) and secure remote access for web applications hosted on-premises environments without complexities. This makes your life easier as you won’t need those complicated reverse proxies or Web Application proxies (WAP) that are usually sit in the DMZ.
Objective:
In this scenario, the idea is to guide you through on how to publish ADFS service externally so that users can access your applications outside of the internal network. This will also be beneficial for public user scenario such as Azure AD users and Azure B2B. The known approach to publish ADFS externally is “to have a Web Application Proxy” server configured in DMZ but that’s very time consuming and over complicated for basic requirements (unless you have specific needs to depend on WAP or Reverse proxy).
This post assumes that you have an ADFS server/s configured and in the running conditions as we won’t be going through that part of the configuration on this one.
Prerequisites:
- Active directory domain and DNS configured in your on-premise environment
- ADFS Server installed, configured and running
- Verifiable public domain name (i.e. mscloudjournal.com)
- Public SSL certificate binding is done in the ADFS server
- Azure tenancy with Azure AD Premium P1 or P2 license
Step1: Download and install proxy connector in the desired server
First thing is first, let’s download the proxy connector tool from Azure. Simply login to your Azure tenancy and navigate to Azure Active Directory –> Application Proxy –> Hit that nice little button to download the latest version of the tool.
Copy across this to your ADFS server (or any desired server that you’re planning to run this connector. You do not need a dedicated server for this as it’s a very lightweight service).

Once copied across to the desired server (ADFS server itself in this case), run the tool to begin the process.

Next, you’ll be prompted to sign in to Azure AD. Make sure you have appropriate privileges to run this operation in Azure AD.

It won’t take more than a couple of minutes.

And there we have the greenlight. Simply close this wizard now and switch back to Azure AD.

Hit refresh and you’ll notice our brand new connector is now up and running in Azure. And we also have a public IP assigned to it by Azure.

Step2: Configure an App in Azure
Now to configure an app using the option given in the top ribbon. Hit “Configure an app” to begin.


Input the details below to suit your environment’s naming. Choose “Passthrough” for Pre-authentication method and the rest can be defaults unless you have a specific need.

And that’s it! our new on-premises application is created successfully.

Step3: Adding the DNS CNAME record
Now we need a DNS record to point the traffic to Azure App Proxy service endpoint. This is done in the DNS repository so you’ll need the access to your domain’s hosting provider (i.e. Godaddy) to add a DNS pointing record.
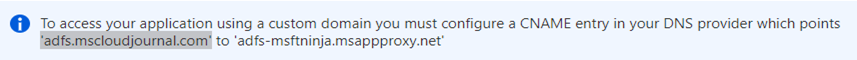
The record will look something like this. Point to needs to be the address we saw in Azure ending with “msappproxy.net” (this is the proxy service endpoint for Azure). Add a new CNAME record as shown below and amend the naming to suit your record.

Step4: Binding the exported certificate
Now lets head over to “Enterprise Applications” –> All applications –> select the app one we created in the previous step (ADFS External Publishing Proxy) –> Application Proxy.

Here you get the certificate upload option. This certificate is taken from the ADFS server. Follow the next step to obtain this from the server.

Export the certificate from the ADFS server
Login to your relevant on-premises server (ADFS server in my case) and open mmc (type “mmc” in the run command and enter) and add the certificate snap-in to the mmc console.

Chose the right certificate that binds to the ADFS service URL and right click –> All tasks –> Export


You need both certificate + the private key so export it from the certificate export wizard in the server itself.



Choose “AES256-SHA256” for encryption and check the password option to enter a password.

Give the cert a name and save it in a secure space. We will upload this to the app we created in Azure, next.

Now lets switch back to Azure AD –> Enterprise Applications –> All applications –> select the app one we created in the previous step (ADFS External Publishing Proxy) –> Application Proxy.
Scroll down and click on the option that allows you to upload the certificate.

Chose the file we exported (.pfx) and input the same password specified when exporting it –> hit upload.

It should like below if everything went well.


And, that’s it ! we should now be able to test it out.
Step5: Testing the external accessibility
To test it, simply try to access the ADFS signon URL from a external network and if you can see the following screen with a validated certificate, you’re all done !
https://adfs.yourdomain.com/adfs/ls/idpinitiatedsignon














































